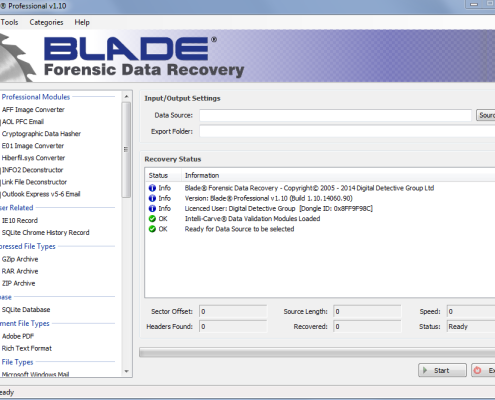
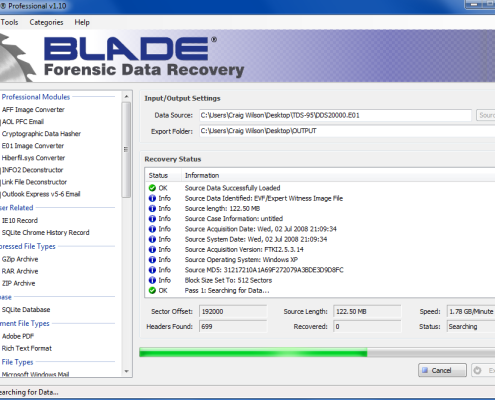
Blade® is a Windows-based, advanced professional forensic data recovery solution. It supports professional module plug-ins which give it advanced data recovery and analysis capabilities.
The power and flexibility of the tool can be expanded as new modules become available. Blade supports all of the major forensic image formats and is more than just a data recovery tool. The professional modules have in-built Intelli-Carve® validation and interpretation routines to assist with accurate data recovery. Some of the standard profiles also have Intelli-Carve® validated routines (such as the JPEG and MPEG-4/3GP/ISO base media recovery module).
The software has been designed for extremely fast/accurate forensic data recovery. Not only is it highly effective in the pre-analysis stage of a forensic examination, it can be quickly configured to recover bespoke data formats. It has specifically been written for the field of Digital Forensics.
Advanced Carving with regular expressions
Blade has been designed for extremely fast/accurate forensic data recovery and with the use of its advanced regular expression pattern matching, high speed carving is exactly what you get. Not only is it highly effective in the pre-analysis stage of a forensic examination, it can be quickly configured to recover bespoke data formats.User Created Data Recovery Profiles
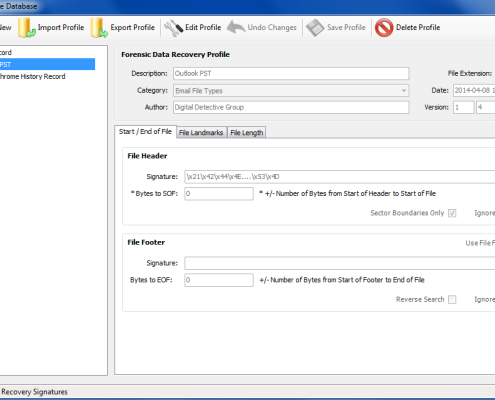
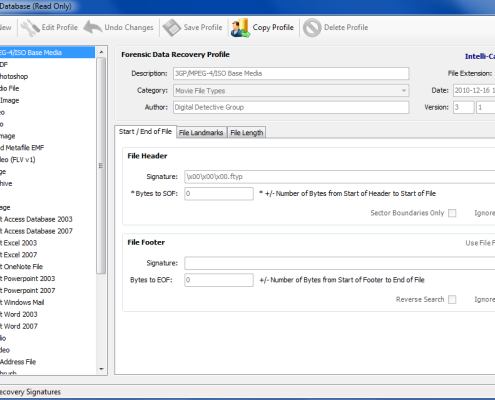
Blade® supports user created data recovery profiles. If a new data type is identified, the user can create a data recovery profile specifically for recovering that new data type. This makes the software extremely flexible. Unlike some command-line carving tools, Blade® offers a fully graphical user interface and makes it extremely easy to create a recovery profile. In addition, they can be exported/imported, which makes it ideal for sharing profiles with other users.Intelli-Carve®
Intelli-Carve® is an innovative, leading edge technology designed by Digital Detective which is designed to increase the accuracy and integrity of the data recovered during the data recovery process. The Intelli-Carve® engine understands the structure of various file formats and can direct the recovery process to ensure accurate data recovery. It can also verify the integrity of the recovered data and logs any data fragments which fails validation.
Professional Modules
With the addition of our professional modules, Blade® can recover data which is not extracted by other forensic tools or traditional carvers. Professional Modules add a powerful capability to this product. Blade® is also ideal for practitioners (or technicians with limited forensic training) who want to perform quick and easy data recovery without resorting to using scripting programming languages or tying up their main forensic tool.
Mobile Phone Forensics
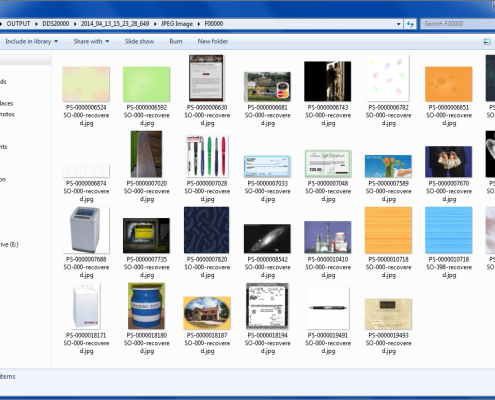
Blade® is particularly effective in mobile phone forensics. It can quickly and accurately recover pictures, video and SQLite databases from mobile phone hex dumps.